Getting your Trinity Audio player ready...
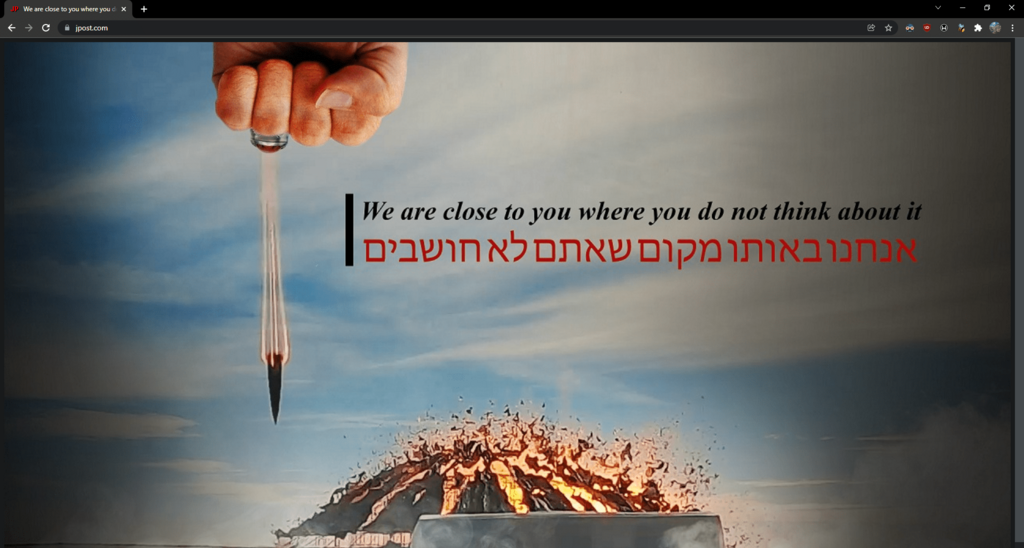
Early Monday morning, the homepage of The Jerusalem Post was hacked to feature an image of the Dimona nuclear facility in southern Israel being blown up.
The image was accompanied by text in both English and Hebrew, reading, “We are close to you where you do not think about it.” The website and Twitter account of The Post’s sister newspaper, Maariv, were hacked with the same image. Both sites were quickly restored.
The sites in question were targeted on the second anniversary of the assassination of Iranian General Qasem Soleimani, who was killed by a U.S. drone strike in Iraq. Soleimani was the commander of the Quds Force, a U.S.-designated terrorist group that acts as the foreign operation arm for Iran’s Revolutionary Guard.
A number of attacks on Israel linked to Iran have made headlines in recent months. In October, an Iranian hacker group is known as Black Shadow reportedly broke into the servers of Israeli internet hosting company Cyberserve, resulting in several popular websites getting taken down temporarily. The same group also stole a massive trove of information from Israeli insurance firm Shirbit in December 2020, which is then sold on the dark web after the company refused to pay a ransom.
Itay Levy, co-founder, and chief technology officer at KERNELiOS, an Israel-based cyber command training center that offers courses and qualifications in an array of cybersecurity-related fields, believes that Israel is ahead of the game when it comes to combating cyberattacks.
“In Israel, the situation is rather good, but around the globe, the problem is more severe because there are a lot of companies that don’t even have the knowledge to be able to understand what they need in order to protect their environments,” Levy said.
KERNELiOS recently announced that the cloud platform will help train experts in Argentina, Colombia, Brazil, Chile, and Panama.
The aim of attacks like the one that took down the Jerusalem Post and Maariv websites, Levy said, is to both demoralize Israelis and discredit Israel’s claim of being a cyber superpower.
“The Iranians want to show the world that Israel is not a ‘cybernation’ as it [proclaims] itself to be,” he said. “They want to show [Israeli] citizens that their data is not as secure as they’d like to think.”
Professor Isaac Ben-Israel, a retired major general in the Israel Defense Forces and the director of Tel Aviv University’s Interdisciplinary Cyber Research Center says the idea that there is a cyberwar between the governments of Israel and Iran is “very much exaggerated.”
While Israel and Iran blame each other for such attacks “no one really knows who did it. When we say Iran it is very difficult to know who in Iran,” he said. “You are not sure if it is done by a group of hackers or by the government.”
Ben-Israel, who is often referred to as the father of Israel’s cybersecurity industry and is one of the country’s top experts in the sphere, says that the damage inflicted by attacks attributed to Iran has been “negligible.”
This does not mean, however, that such cyberattacks can be ignored, he said. The cyberattacks have not been very successful or damaging because of the measures Israel has taken to prevent them, Ben-Israel said.
“We should continue doing whatever we do to prevent the success of these attacks,” he said, adding: “There are many attempts.”
Ben-Israel says that in most cases, websites that can be hacked easily can also be protected easily, but sometimes the owners of such websites often ignore the need to take precautions because they do not feel threatened. Other important measures include having a backup of information in order to quickly restore the hacked website.
The more serious cyberwar, however, is not taking place in the civilian sphere. Several attempts have been made in recent years to disrupt Israel’s critical infrastructure, though these attacks were generally not widely publicized, Levy noted.
For example, he said, “the electricity was shut down and also cellular companies ceased to work for several hours and even days. There were also some water companies that were attacked. The Iranian government is trying to reach Israel’s critical infrastructure in order to disrupt daily services.”
Ben-Israel agrees that cyberattacks “can be serious,” citing the offensive on Israel’s water supply, including an attack in April 2020, in which Iranian hackers sought to cripple computers that controlled water flow and wastewater treatment for two rural districts in Israel, allowing an increase the amount of chlorine in the water supply to dangerously high levels.
The attack was countered before any serious damage could be caused. Three months later, another attack emanating from Iran targeted agricultural water pumps in the upper Galilee and another struck infrastructure in the center of the country.
Israel, for its part, also has made use of its cutting-edge technology and expertise in an attempt to upset Iran’s nuclear program, with alleged cyberattacks causing disruption to the operation of centrifuges, damage to the electrical systems in some nuclear facilities, and causing explosions.
Nevertheless, Levy does not believe Iran represents a very serious threat to Israel, which he says is more secure than other nations.
“Israel as a whole is aware of the risk of a cyberattack,” he said. “But, if you’re determined as a nation to do harm, you can do it. I’m not foreseeing that they can shut down the whole country, but even if an Iranian attack would succeed only for a few hours then it would do some harm.”
Ben-Israel adds that Iran is not a threat because of its sophistication – most of its attacks amount more to harassment than damage, but because it is motivated. Israel is a target because “they don’t like us,” he said.
In addition, Ben-Israel points out that new cyber threats are always right around the corner. They change very quickly because “every day there is a wise guy with a new idea.” And those ideas can become a threat in just four to five months, he says.
The article was written by Maya Margit and reprinted with permission from The Media Line