Getting your Trinity Audio player ready...
Iranian hackers on Tuesday posted files allegedly containing private information on hundreds of IDF soldiers.
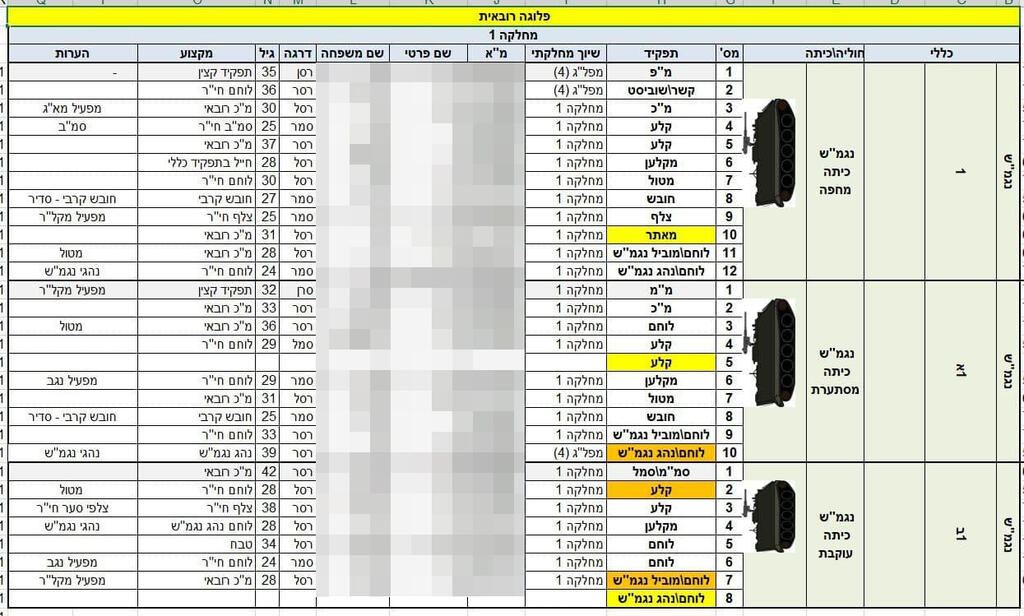
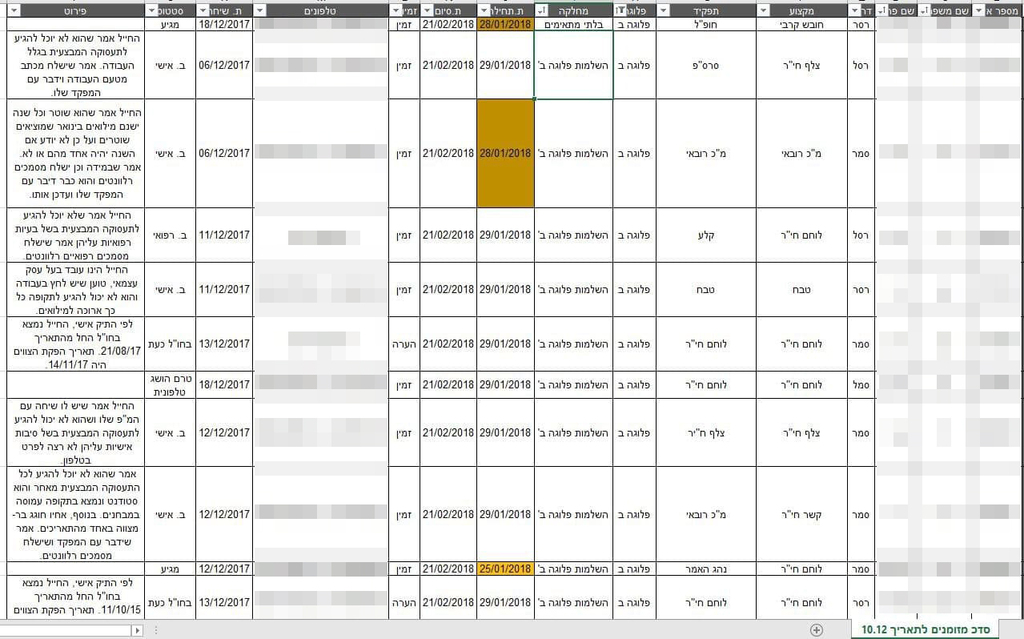
The files, leaked by a hacker group named "Moses Staff", also contain details of the deployment of an IDF combat brigade, including job descriptions, a full list of names, e-mail addresses, phone numbers, and residential addresses of members of the brigade.
Photos of Defense Minister Benny Gantz were posted by the group on Monday, along with a threat that he is being surveyed by the hackers.
"We know every decision you make and will hit you where you least expect it. We have secret Defense Ministry documents, operational military maps and troop deployment information and will publish your crimes to the world," the hackers said in their post.
All the information was posted on the dark web and in groups of the Telegram messaging app.
Some files have details of reserve IDF soldiers and military units, including names, ranks, military roles, and their correspondence with their units, explaining why they were unable to show up for duty.
Other files consist of information on thousands of teenagers set to enlist in the IDF, including those in pre-service programs.
Besides names, addresses and phone numbers, the files contain sensitive personal information such as psychological information and the socio-economic status of the soldiers' families.
The group's hacks are carried out through the use of bots and include warnings such as "your end is near."
Moses Staff also published a series of leaks containing databases with information on thousands of Israelis, which was stolen from the computers of a number of private companies. Cybersecurity experts say those hacks are aimed to influence consciousness, just like the groups that hacked Shirbit company on December 2020.
The leaks of the new group are characterized by explicit aggressive texts such as "We continue to fight until we discover your hidden crimes, your end is near."
The Israel National Cyber Directorate said on Wednesday that they have warned of the risk posed by security weaknesses in some organizations.
"We call upon organizations to implement the latest critical updates that Microsoft has released to deal with these weaknesses, which is a simple, free update that can reduce the risk of this attack.”