Getting your Trinity Audio player ready...
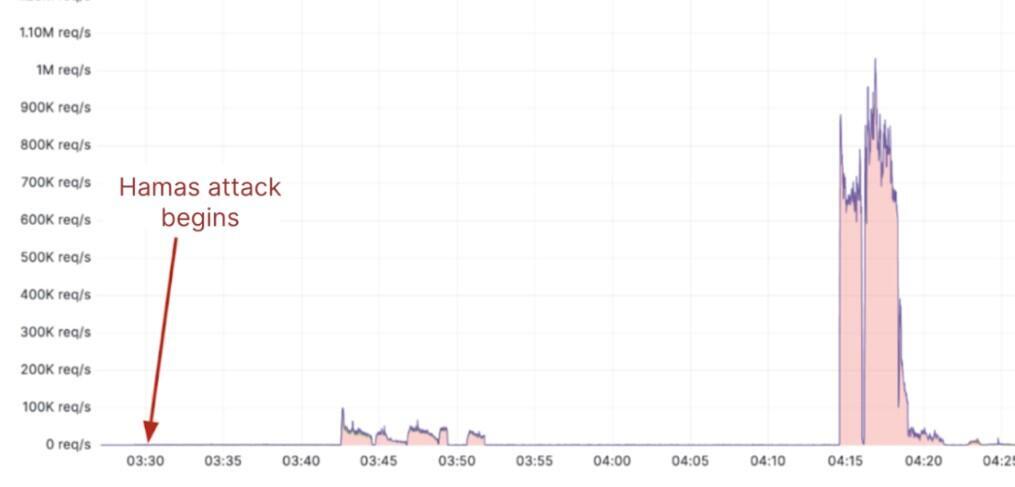
During the Israel-Hamas conflict, the digital dimension became one of the most active fronts, as highlighted by a report from the internet company Cloudflare. According to the company, which specializes in protecting websites and companies from Distributed Denial of Service (DDoS) attacks, massive DDoS attacks began targeting numerous Israeli online platforms, particularly media outlets and software companies, as Hamas terrorists entered Israeli border towns on the morning of Saturday, October 7.
Read more:
While the terrorists breached the fence around 6:30 in the morning, this was accompanied by relatively low-intensity attacks of about 100,000 connection requests per second. However, about 45 minutes later, a focused and massive attack began with approximately one million connection requests per second - an unprecedented intensity not seen in previous confrontations with Hamas. Connection requests are attempts to access a website, online service, application or even a company's internal network.
Ground invasions accompanied by massive denial-of-service attacks have been observed in several wars involving Russia in the past, especially during Russia's invasion of Georgia and its two invasions of Ukraine (in 2014 and 2021). This approach is consistent with a well-known doctrine in Russian warfare: targeting critical infrastructures such as electricity and rail while simultaneously launching ground and aerial invasions.
It's unclear whether Hamas or Iran were merely inspired by this Russian warfare doctrine or if they received discreet assistance from Russian or pro-Russian entities. Numerous pro-Russian hacker groups known for their ties to the Kremlin have started targeting Israeli assets in recent weeks.
A significant portion of Hamas' cyberattacks targeted apps that issue warnings about security incidents. The hacker group AnonGhost, associated with pro-Palestinian activities, exploited a vulnerability in the Red Alert app and sent fake messages such as "Nuclear bomb on the way" or "Death to Israel." Another Red Alert app was counterfeited, and malware was implanted that stole the personal data of users who downloaded it.
Additionally, the English-language Jerusalem Post website was attacked and was effectively unavailable for three days from the onset of Hamas' aggressive operations. This clearly represents an attempt to silence the reporting of events from the Israeli side to the international community.
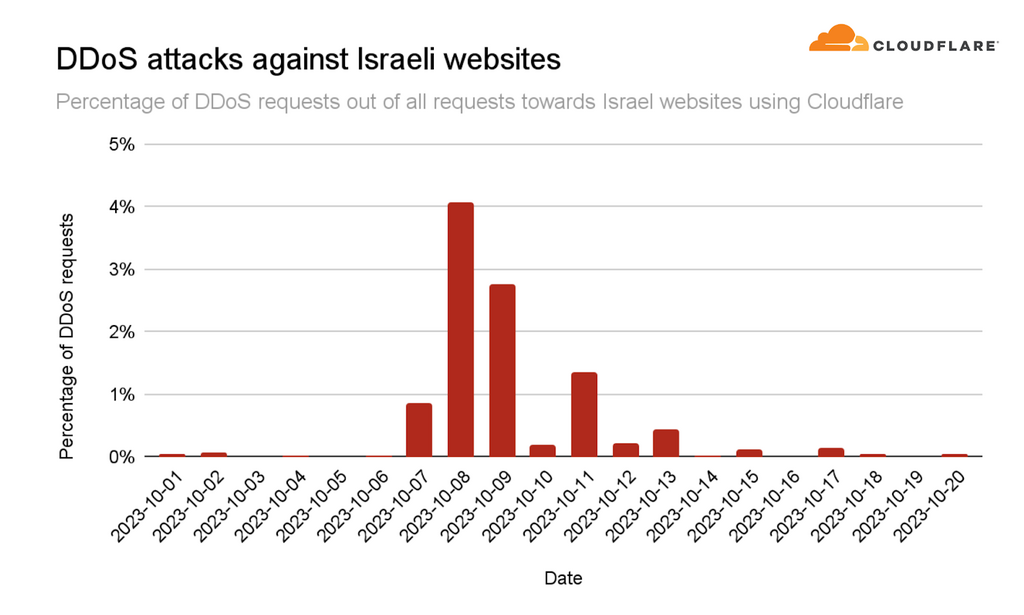
DDoS attacks continued at full force for approximately six days until October 12, at which point they declined to a level of less than one hundred thousand connection requests per second. As mentioned, more than half of these attacks were directed at media websites and apps.
The same tactic was observed during the invasion of Ukraine – intense attacks on media websites and applications. The aim, it seems, is to prevent the attacked side from relaying critical information to its citizens in the affected areas. However, it's unclear why the hackers targeted software companies. The assumption is that perhaps they were trying to gain access to databases or online services operated by them. In third place, far behind, were banking and financial sites, and in fourth place were government sites.
However, it wasn't only Israeli Internet that came under attack; Palestinian websites experienced the same onslaught. Cloudflare did not disclose the origin of these attacks, but according to the company's data, there was a significant spike compared to the days before October 7.
On the day of Hamas's attack, approximately 46% of all traffic to Palestinian sites was identified as DDoS (Distributed Denial of Service) attacks. Two days later, this number jumped to around 60% of the total traffic. Most attacks were directed at banking sites, likely aiming to disrupt Hamas's financial transfers. The second primary target was internet service companies. Media outlets were also attacked, but to a much lesser extent.