Getting your Trinity Audio player ready...
Alongside the bombings, assassinations and ground operations, another war is taking place between the two main constituents of the Axis of Evil and Israel—and it is sophisticated, cruel and no less dangerous. A secret operations center located in the Shin Bet headquarters called "HaOrgan" is leading these covert battles.
Hacker groups such as Lebanese Cedar and Handala are targeting essential infrastructures in Israel, collecting sensitive confidential information or hacking into the computers of the National Security Ministry and Prime Minister Benjamin Netanyahu's Facebook account, and this is just the beginning.
This is what the battlefield looks like where the weapon is a keyboard and the ammunition is code lines, while the goal being the same: to hit as much as possible and to get hit as little as possible
Inside the Shin Bet headquarters in northern Tel Aviv, operates one of the least known and most significant operations centers responsible for Israel's security. It is called "HaOrgan," and for the past year, it has been waging a separate, covert war only known to a few, namely, Israel's cyber warfare against Hezbollah and Iran.
Around the table at HaOrgan gather representatives of the Shin Bet, Mossad, the IDF, the Military Intelligence Directorate, the Defense Ministry and the Israel National Cyber Directorate. Before the war, HaOrgan would meet once a week for an evaluation session. Over the course of the war, it operated continuously 24/7 and conducted like the pit at the Defense Ministry headquarters: the screens display a picture of the current cyber warfare and provide reports from both civil and military officials about online attacks, as well as intelligence about planned attacks.
The cyber experts at HaOrgan categorize them according to their degree of severity: starting from non-threatening attacks, through manipulations and attempts to recruit spies and agents, to cyber attacks that could pose a real threat to the State of Israel, targeting essential infrastructure such as power plants, water and communication systems or attempts to hack into sensitive confidential databases.
HaOrgan members decide in real-time, depending on the risk involved, what to do in each case. Attacks on civilian infrastructure, for example, are transferred to the handling of the National Cyber Directorate. Attempts to either recruit spies or generate terrorist acts are transferred to the Shin Bet and Mossad.
When HaOrgan spots the source of the attack, they can instruct a counterattack. In most cases, this would be a cyber attack; but there are occasions when HaOrgan will ask the IDF to bomb a certain location, such as a server farm, or to eliminate a cyber expert.
"In these cases," says a senior security official, "the Israeli Air Force would intervene, launching its missiles." That is why Hamas' cyber apparatus, which did not pose too great a threat to begin with, was swiftly eliminated.
Hezbollah's cyber array, on the other hand, was damaged, but it is still very active and conducts cyber attacks. And of course, the most significant active cyber apparatus of them all, that of the Iranians, has yet to demonstrate its true capabilities.
The numbers are jaw-dropping. Since the start of the war, Israel has faced thousands of attempted cyberattacks every day. Most of them are not critical, but they certainly show the extent of this covert war, which is being pursued alongside the overt one.
Take, for example, one of the most prominent targets attacked: the Prime Minister's Office. In April 2024, the State Comptroller published an audit report on data safety in the Prime Minister's Office. It turns out that in the first five months of 2023, before the war broke out, there were 49 million attempts to hack the remote connection to the Prime Minister's Office, more than a million distributed denial of service (DDoS) attacks, about 9,000 attempts to exploit loopholes in the system's protection and more than six million e-mail messages that contained malware or malicious links.
The Prime Minister's Office reported that all attempts were thwarted, but the State Comptroller found that the cyber protection at the Prime Minister's Office was insufficient and "could lead to substantial damage to the State of Israel in terms of political, security, economic and image aspects."
The report fails to mention a particularly unusual event that took place last April: an Iranian cyber hack into the prime minister's Facebook account, which was accompanied by a video featuring Arabic verses from the Quran and texts in Persian. The post was removed a few minutes later, and apparently, no harm was done, apart from the great embarrassment.
"Since the beginning of the war, there have been seven times more cyberattacks than before," the senior official Ynet's sister publication Yedioth Ahronoth, "and this happens at the same time as the "conventional" kinetic war is ongoing. "The command-and-control center identifies these cyberattacks, suppresses and thwarts dozens of attacks per day. These things are not disclosed to the public."
But not every cyberattack is thwarted.
"In the last two years, there has been a dramatic change compared to the previous period. Until then, the enemy collected information and became acquainted with Israeli society, but now they have moved to the next level and become active. Our ability to get offensive and defensive information has greatly improved, we made a big leap, but we still have a long way to go."
Hezbollah and Iran's hackers have also recorded a series of successes in recent months, including hacking into Ziv Medical Center in northern Israel, breaking into the government email server (MailGov), hacking into the National Security Ministry's website, hacking into several commercial entities, including large law firms, and more.
So, while Israel finds itself neck deep in an intense and overt war on seven fronts for over a year, it is simultaneously waging another war in the shadows, much less known—but one that can be no less destructive, and sometimes even more.
The pink button
June 2010. The control units of the centrifuges at the uranium enrichment facilities in Iran begin to speed up and slow down uncontrollably. Some centrifuges are damaged and others, according to reports, are destroyed. The Iranian nuclear project suffers a blow. The Iranians are confused until it turns out they were attacked by a mysterious computer virus, named by global media "the Stuxnet worm."
To this day, this is considered one of the most significant and devastating cyberattacks in the short history of cyber warfare. Reports around the world attribute the sophisticated attack to a collaboration of Israel and the U.S.
The Iranians learned their lesson, and in the years that followed, their investment in defensive and offensive cyber jumped manyfold. The Iranians want to become a cyber powerhouse, and for that purpose, they are training cyberwarriors quickly, setting up new attack and defense systems and purchasing technology from wherever possible.
The gap between Iran and Israel in the cyber arena is still far from being closed, but in the middle of the previous decade, the Iranians also began to launch significant cyberattacks. According to foreign publications, in April 2020, they attempted to hack into the industrial control systems of Israel's water pumping system and raise the level of chlorine in the water supply. The attack was discovered in time and thwarted, the Iranians refuted all evidence of their involvement.
Days later, an Iranian shipping port was shut down for many hours. Israel did not take responsibility for the attack.
The Iranians share some of their knowledge and the cyber technologies they have obtained with Hezbollah, which has established several hacker groups. Some engage in cyber activity routinely and others build what is known in the cyber world as "red buttons," a specific cyber capability built over time to be "pressed" when necessary and activate a one-time attack. After activating it—the "red button" is burned.
Israel's operation to blow up pagers and walkie-talkies in Lebanon, for example, is such a "red button." It's safe to assume that Israel has more "red buttons," but that the Iranians have also built their own and may activate them if the war escalates.
The Hezbollah-backed hacker group Polonium was exposed in 2022; it coordinated with actors affiliated with Iran’s Ministry of Intelligence and Security to develop "red buttons" against Israel's defense industry, government offices and critical infrastructure. The group targeted more than 20 organizations in Israel. It is unknown if any significant damage had been done.
Microsoft detected the group and successfully disabled the offensive activity abusing its OneDrive service. Polonium's success was temporary. Security firm ESET later said in a report that Polonium’s toolset consisted of seven custom "backdoors" deployed in various programs to gain access to the victim’s network.
The Hezbollah-backed group also developed other malicious modules for espionage, logging keystrokes, taking screenshots, executing commands, taking photos with the webcam or exfiltrating files, and it is likely to continue developing new tools.
9 View gallery


Lebanese first responders evacuate Hezbollah member hit in pager attack
(Photo: REUTERS/Mohamed Azakir)
According to ESET's report, Polonium's main purpose was to spy on targets and collect confidential data. It doesn’t seem to engage in any sabotage or ransomware actions, but it is impossible to know what other "red buttons" the Iranians have.
Sanaz Yashar, CEO of Zafran Security, served in IDF intelligence Unit 8200 and is considered one of the greatest experts in Iranian cyber. "I suggest not to underestimate the operational cyber capabilities of the Iranians," she says. "Efforts are being invested in stopping it, but I don't think the Iranians have said the last word, they haven't gone 'all in' yet. Once they do, we will probably feel it very well. You can be sure both sides have more capabilities than you have seen so far."
Yashar says it's time to talk about a different kind of "buttons," called "pink buttons." These are cyberattack systems that work continuously, mainly to signal to their target "Listen, I have an even worse weapon."
"The most significant cyber warfare that I have seen so far is against the U.S.; my jaw drops when I see what the Chinese are doing to American infrastructure. Did someone press the red button? No. It's all about 'pink buttons.' You develop a red button, but you don't press it. You just want to deter the other side, but we haven't yet reached the point where someone turns everything off for someone. The rules of the game are more about exerting influence over politics and less about decisive actions," Yashar says.
The most alarming hack
So, while Israel and Iran, with its affiliate Hezbollah, pursue relatively low-intensity cyber warfare, and both sides are developing "red buttons" and "pink buttons," October 7 happened. At once, the number of cyberattacks on Israel spiked.
"HaOrgan" classifies three main cyber arenas. The first involves attacks on critical infrastructure such as power plants, refineries, banks and more. The second involves attacks on government offices and companies in the private sector. The third engages in psychological manipulation through propaganda on social media, information theft, espionage and agent recruitment efforts.
Officials with whom we spoke admit that all of Israel's critical infrastructure is under constant attack, but none has been damaged so far. Cyber experts from the private sector, however, used less unequivocal phrasing—"barely damaged," which implies that some of Israel's critical infrastructure was indeed damaged to some extent but not disabled.
And no other piece of infrastructure in Israel is more critical than the nuclear reactor near the southern city of Dimona. And yet, the infamous hacker group Anonymous managed to infiltrate the reactor's computer system last March and steal information. They made the attack public and rejoiced on social media.
Anonymous is not affiliated with either Iran or Hezbollah, having targeted the former in the past. This is not the first time it has made Israel a target, and various hacker groups use this name. Although the data stolen from the reactor did not harm Israel's national security, it did land a psychological and image blow to Israel which failed to protect one of its most sensitive sites.
In October, the New York Times reported the arrest of two Sudanese nationals operating as Anonymous Sudan. According to the report, on the morning of the October 7 massacre, the group disrupted Israel’s Red Alert system, an app designed to warn civilians of incoming rockets or terrorist infiltrations, using a DDoS attack.
But these are minor attacks. Last March, the Israeli government's e-mail service MailGov was hacked and disabled, and large amounts of correspondence from all government departments were leaked. The Cyber Directorate confirmed that while emails were leaked, none were considered classified.
A month later, the Justice Ministry's servers were hacked and massive amounts of data, including documents and personal details of judges and ministry staff, were leaked.
Again, Anonymous claimed responsibility for these attacks. The group claimed that it also broke into Israel's National Insurance Institute, Israeli banks, and IDF computer systems and downloaded large amounts of data. It can be assumed that some of these statements are false and were intended for psychological warfare.
Nevertheless, some of the cyberattacks did take place. Recently, the State Comptroller published an audit report, stating that he found, among other things, significant deficiencies in the cyber security of the National Insurance Institute. The Comptroller found that every day there are tens of thousands of attempts to attack the National Insurance website.
One hacking group affiliated with Hezbollah is Radwan Cyber Pal, named after the commando force of the terrorist organization. On October 6, it managed to hack the National Security Ministry, accessing sensitive information on thousands of applications for a personal firearm license, documents that include details and certificates of the applicants. The group also published the following message: "The Radwan Cyber Pal, targeted Israel’s National Security Ministry. We have the full data of the Occupation settlers and soldiers, in addition to many confidential documents."
Iranian and Lebanese hackers also tried to break into Israeli hospital websites, whose databases include a great deal of sensitive patient information. In November 2023, a particularly severe cyberattack was launched at Ziv Hospital in Safed. It took the Israeli authorities three days to identify the attack and halt the information leak.
Nevertheless, during this time, the hacker group Agrius, affiliated with the Iranian Ministry of Intelligence, and Hezbollah's cyber unit Lebanese Cedar managed to download and publish hundreds of thousands of medical records of patients, including information about wounded soldiers. This event was so unusual, that the Israel National Cyber Directorate published a rare and detailed message stating the identification of the hacktivists and the damages inflicted, warning that the data extracted might be published by the attackers.
Another hospital came under attack last February. This time it was Rambam Health Care Campus in Haifa. The Health Ministry and Israel National Cyber Directorate reported that the attempt was blocked without any damage to the hospital’s computer systems or overall operations.
"Today there are many small hacker groups and some central ones that engage in leaking information," says Erez Dasa, who runs the Hebrew-language cyber news Telegram channel CyberSecurityIL. "Not all leaked information is published immediately. The groups keep the information and use it at a time convenient for them. They get their hands on information at some point and they decide when to publish it."
Get the Ynetnews app on your smartphone: Google Play: https://bit.ly/4eJ37pE | Apple App Store: https://bit.ly/3ZL7iNv
The situation of the Israeli economy in this respect is no better. Various companies were attacked this year, such as Israir Airlines, IKEA, Home Center, Keter, Israeli public broadcaster Kan, law firms and the list goes on and on.
The attack methods were usually similar, albeit causing different kinds of disruptions; some caused no damage, in other cases the hackers managed to download large amounts of documents and customer records and sometimes the companies' websites were taken down. "Some damage does happen, and most of these incidents don't even make the headlines and you don't hear about them, but I'm telling you that cyberattacks are carried out daily," says cybersecurity consultant Shlomi Cohen.
"Israel National Cyber Directorate tries to close the loopholes, but we are always one step behind. Gaining awareness of cybersecurity stems from the same mindset involved in the need to have data backup," says Cohen.
What does it mean?
"As long as you're not attacked, chances you'll do something about it are low."
Psychological warfare
A large part of cyberattacks against Israel during the war was that is known as "psychological warfare." These attacks are not intended to obtain data and information nor to damage infrastructure, but rather to impose psychological effects.
The tactics of these cyberattacks are varied and may be "vandalistic," in which hackers break into a website and deface it or leave a message. In December, the IDF's website was attacked by pro-Palestinian hacktivists who replaced the site's homepage with a threatening message: "You will find nothing from us but killing and terror," wrote the hackers, among other things.
9 View gallery
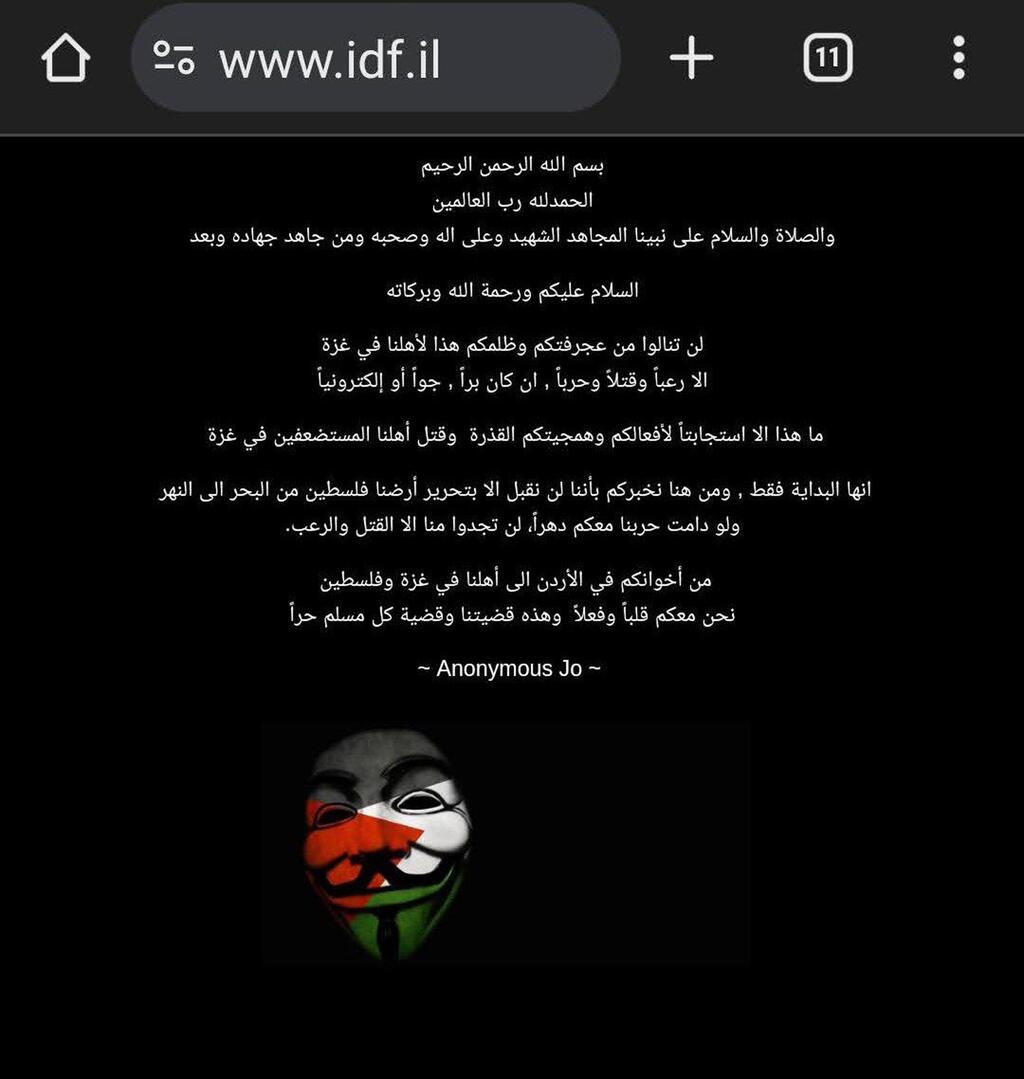

IDF website hacked, with the message 'You will find nothing from us but killing and terror' displayed on the homepage
(photo: Screengrab)
A similar message was also left on the Israel Post website which was also attacked and vandalized. The damage in both cases may be minimal, albeit causing great embarrassment.
Yoram Hacohen, CEO of the "Israeli Internet Association (ISCO-IL)," talks about a new psychological warfare, which involves attempts to "steal" Israeli websites. "We have seen attempts to take over Israeli websites and replace them by redirecting users to Hamas or Hezbollah websites."
Did they succeed?
"They did in some cases, because they managed their digital assets carelessly." ISCO-IL was able to block these attempts and cancel the site redirecting that had already been carried out, added Hacohen.
More well-known and popular psychological operations are carried out via social media, which aim to incite and create social tensions, mainly by conveying political messages.
Recently, there has also been an increase in attacks in the form of SMS that are sent to mobile phones, sometimes bearing the name of the owner of the device, in order to create a sense of threat. Last month, for example, millions of Israelis received fake SMS messages, supposedly from the Home Front Command, urging them to immediately enter protected areas. The SMS messages included a malicious link.
Another message, sent under the name "Sinvar" (a misspelling of Hamas leader Yahya Sinwar's name), read: "Sinwar's murder has opened the gates of hell for the Jews."
Fax machines are also used for psychological warfare purposes. "Today is October 7, the great day," read a message many fax machines in Israel emitted. "Your Prime Minister Netanyahu left you to die... Wait for us, we are coming to kill you all." The message included a barcode to scan, which led to a propaganda video clip.
The leading Iranian hacking group in such psychological warfare is probably Handala, named after the famous character, created by a Palestinian newspaper cartoonist, which has become the symbol of Palestinians.
The group carried out a long series of cyberattacks, including breaking into the computers and private phones of politicians and military personnel and publishing their private photos, sometimes embarrassing ones.
Handala is considered particularly dangerous and sophisticated, and engages in other areas of hacking, including ransomware and stealing databases. It relies mainly on phishing campaigns, but unlike other hacker groups, some of Handala's messages are in Hebrew at a very high level.
In one of its latest attacks, Handala broke into a small Israeli company, which had access to send SMS messages to five million Israeli citizens. Handala rushed to take advantage of the 'treasure' and sent a threatening message to millions of Israelis which read: "The meeting is over, we heard the conversations! Our message is clear, don't be stupid! Handala." It may not be harmful, but it certainly causes fear and mistrust.
9 View gallery
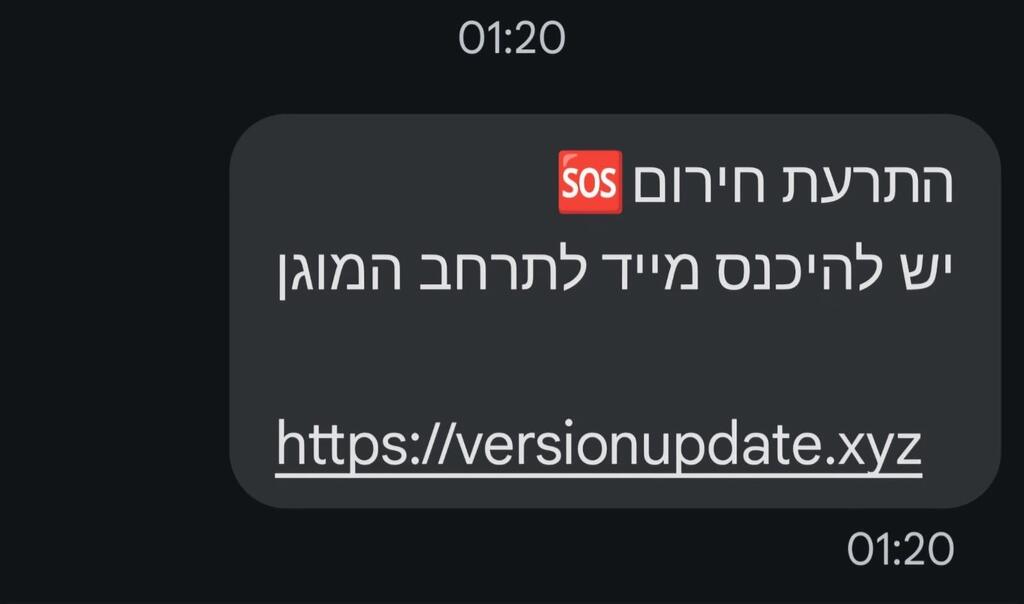

Typo-ridden text message, likely from Iran or Hezbollah, featuring malicious link sent to Israelis during the war
(Photo: Screengrab)
It is precisely these types of attacks that usually fall through the cracks, and currently, there is no Israeli body to defend against this psychological warfare. However, there are civil organizations that aim to combat these malicious cyber activities, such as Fake Reporter, which systematically exposes Iranian bots on social media, or the Israeli Internet Association (ISOC-IL), which operates the Internet Safety Hotline to deal with the problem.
"We receive requests for assistance from citizens who are attacked via WhatsApp, usually caused by pro-Palestinian hacking organizations," says Edan Ring, VP of community and social affairs at ISOC-IL. "They make use of the information they collect to manipulate, sow demoralization and panic."
For example?
"For example, the distribution of professional video clips displaying attacks on Israeli Air Force's control unit, or UAV attacks they executed. They really invest in edited videos using graphics and titles in Hebrew. Sometimes it's fake content, like their claims about attacks that didn't happen or the killing of hostages."
How do they manage to infiltrate our phones?
"Today it is very easy to locate lists of Israeli phone numbers and e-mails for a fee, and terrorist groups buy huge databases of Israelis. Israel was caught unprepared in dealing with the digital realm. We cannot be protected unless the leaks of the databases are handled."
Can't Israel reach these groups and stop them?
"I think that in the last year our failure to protect citizens, especially on social platforms, has been fully exposed. The country does not have the capabilities to identify foreign and hostile network activity. The Shin Bet and other bodies woke up too late. Israel is also afraid to engage in the regulation of social networks, it does not demand answers nor transparency, nor does it engage in creating a safe digital space for the users."
The Israeli security establishment is very much concerned about the psychological warfare carried out on social networks, but they are more concerned about the next step happening after the threatening WhatsApp or SMS messages are being sent.
The senior security official at Ha'Organ says that Iran's ability to plant harmful spyware on Israelis' phones poses a real threat; "If Israelis do not acknowledge this danger, they will be eventually hit. Iranian and Hezbollah units are planning to do this. I hope that Israeli citizens will improve their level of preparedness. It's like dealing with a suspicious object incident; if people who come across suspicious information will report it and will not cooperate with the attackers, we could deal with it more effectively."
G. served in the IDF as deputy commander of the cyber department at Intelligence Unit 8200. Today he is the VP of an Israeli cybersecurity firm while also serving in the reserves in the cyber field. According to him, Hezbollah has obtained significant intelligence on Israeli individuals and targets.
They use images of attractive girls as avatars to phish for sensitive information from IDF soldiers, offering them intimate pictures if they 'Just tell them in which military post they are serving and when they are going home.' I'm sure they learned a lot about the IDF routine in the Upper Galilee very easily," G. says.
Still, we were afraid that the cyberattacks would be more severe, and while preparing for long blackouts, Israelis were rushing to buy generators.
"If they hit a supermarket chain paralyzing its cash registers, it means that they hit Israel's home front, which will result in mass hysteria. And if such attack is accompanied by SMS or WhatsApp messages, like 'be careful of what we will do to you', this could damage the Israeli public much more than any missile."
Shortly after our conversation with G., a cyberattack compromised the service of an Israeli clearing company Credit Guard, temporarily blocking credit card payments. According to the Israel National Cyber Directorate, the attack was blocked after being discovered, with the service quickly returning to normal. One can only imagine what would be the impact of a cyberattack on the core operations of Israel’s credit card systems.
And there are also Iranian attempts to recruit Israelis via social media, asking them to do various propaganda tasks such as hanging inciting posters, spying or even carrying out assassination plots. In recent months, the media has dealt a lot with the arrest of more than 20 Israelis, most of them Jews, who agreed to become agents for Iran, for money. The real number, it seems, is much higher. "The number of incidents is astonishing," says a senior official in the defense establishment. "It was found that more Israelis turned into Iran spies, and there are Israelis who followed Iran's instructions."
'The Israeli government was oblivious to what's really happening'
Officials at HaOrgan's operations center are very proud of their accomplishments in thwarting significant cyberattacks in the current war. "We entered the war. Cyber warfare is alive and kicking," says Gaby Portnoy, Director General at Israel National Cyber Directorate, "and we were able to protect the State of Israel in the cyber realm. The impact of these cyberattacks was not serious nor significant, and they did not compromise Israel's functional continuity," says Portnoy.
But not everyone agrees with him. "In terms of cyber defense, before and during the Iron Swords war, there were many failures," says a CEO of one Israeli cyber intelligence company, "and no one seems to take responsibility or understand how deep the failure was. The perimeter security of Israeli hospitals was not good enough and this should not have happened. National security systems were breached, such as MailGov and sensitive emails were leaked. It was devastating. This should never have happened."
Another CEO in the cyber field says: "The Israeli government failed to understand what was happening, they were totally disconnected. Organizations, municipalities and companies failed to take measures to ensure the safety and security of their cyberspace. They were busy bringing in all the 'Big Shots' from Silicon Valley, but when technology managed to detect an attack, no one knew what to do with it."
According to G., the number of daily hacking attempts exceeds the number of thwarting successes. "The enemy uses 'Spray & Pray' technique (scanning millions of Internet addresses - IP - and randomly finding unprotected loopholes, hacking, vandalizing and stealing information)," he says. "They are looking for IP addresses of Israelis and attack wherever they can."
Portnoy does not deny the problems involved in dealing with cyberattacks: "The situation of cybersecurity in Israel is not satisfactory, but on the other hand we managed to thwart the numerous attacks. There is a layered and diverse system that can provide a solution. After October 7 we must not be complacent. There are still many things to do, upgrade and improve."
Leaks of email correspondence retrieved from government email servers seem significant and dangerous.
"The information was defined as 'unclassified,' but when such incidents are accumulated, it becomes 'sensitive'. This event was bad and should have been prevented. The question is - where do we go from here? We of course fixed the loopholes, and I hope we improved significantly."
Do you think that following the current cyber war, decision-makers and the general public have a better understanding of the cyber risks?
"Awareness increased during the war, but not enough. However, there's always a dilemma because communicating cyberattack incidents to the public may provide the enemy with a sense of achievement. The tendency is to make it public wherever we can. This is important, it raises awareness. Moreover, we are trying to attribute the attacks to whoever is responsible; we are no longer afraid to say, 'Iran attacked'."
HaOrgan are taking proactive measures, and do not wait for Beirut and Tehran Hacktivists to attack. There is no doubt that cyber war is one of the main arenas in the current war. Some of the tools to handle it are provided by Israeli companies, such as NSO.
"I'm not going to talk about how our tools are used," says Yaron Shohat, CEO of NSO, in a conversation with Yedioth Ahronoth. "Our top-quality intelligence have been successful in locating each and every terrorist, thus we know who to attack, where Nasrallah is, who are his subordinates and where they are located. All this kind of intelligence comes from our worlds. Cyber is the tool that is winning this war, and if the necessity of this industry and tools were not clear until now, I think this is the clear-cut proof."
Do you also know how to target pagers?
Shohat is evading a direct answer. "Nasrallah gave a speech, which was published in all the newspapers, warning his operatives that Pegasus spyware was on their phones, and opted for using pagers instead. After a few months, the pagers exploded. Could it be manipulation? Perhaps someone had an interest in making it public in Lebanon, for everyone to use pagers. There is no doubt that this is still a crazy intelligence achievement, it undermined Hezbollah officials, and it also had a psychological effect making them use other devices, which were about to damage them."
Meanwhile, this week too - like every week for the last 13 months - thousands of attempts to break into essential infrastructures, government websites and indoor companies were recorded at HaOrgan. The cyber directorate understands very well that some kind of political agreement, if and when it is reached, may herald the last rocket being launched in this war - but definitely not the last cyber attack.









