Getting your Trinity Audio player ready...
On October 7, 2023, the Hamas terror organization opened a coordinated, vicious attack against Israel, using rockets and then slaughtering civilians, then taking hostages. Israel woke up to its most devastating terror attack ever.
More stories:
Shortly after this terrorist attack, other anti-Israeli groups attacked Israeli organizations, even though the attack was uncoordinated and we’ve seen more severe DDoS attacks in the past, on this front, Israel’s critical infrastructure and financial services were better prepared than in previous conflicts.
What are DDoS attacks?
DDoS cyberattacks are designed to disrupt critical infrastructure and online services. Successful attacks render inaccessible essential services like the Tel Aviv Stock Exchange, Clalit or Maccabi online, various online banking services such as Leumi, Discount, Hapoalim, as well as home internet and satellite communications. They can also prevent security personnel from accessing their systems and act as a diversion for further cyberattacks.
Who’s attacking Israel?
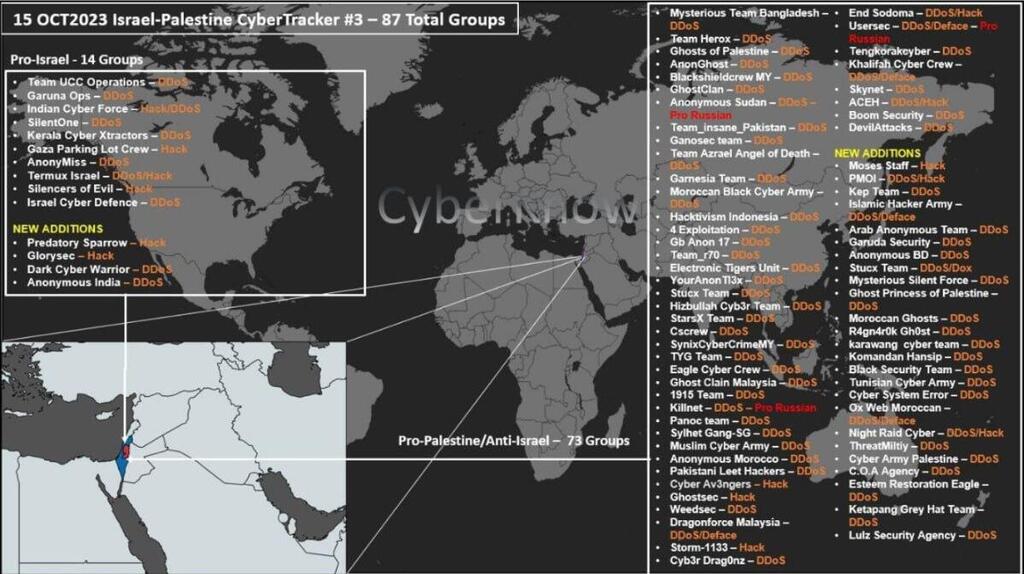
Regarding threat actors, we've identified consistent anti-Israeli and radical Islamic groups that persistently target Israel throughout the year. The primary groups involved in the current cyber assault are the following.
- Killnet – A Russian state-sponsored attack group.
- Anonymous Sudan – A pro-Russian (related to Killnet) anti-Israeli and very active group that has been targeting NATO countries and Israel since the start of the conflict in Ukraine.
- The “Mysterious” groups – This assortment of groups (Mysterious Silent Force, Mysterious Team Bangladesh, etc) are very active pro-Islamic groups based in Southeast Asia, attacking primarily non-Islamic countries and organizations in Asia (India, Thailand and more).
- Team Insane – Another assortment of pro-Islamic groups, working closely with the Mysterious Groups, also based in Southeast Asia with members from Malaysia, Bangladesh, Pakistan and Indonesia.
- Black Cyber Army – An Arab Islamic group, consisting of many subsidiaries and subgroups across the Arab world, attacking Israel and other Western countries.
Before the start of the war, it was evident that Israel isn't the only target of pro-Islamic and anti-Western cyber groups. There's no evidence to suggest the cyberattacks coinciding with Hamas's October 7 assault on Israel are orchestrated by the terrorist group. Rather, they appear to be more of an immediate reaction from various anti-Israel groups.
Critical infrastructure better prepared this time
There remain numerous aspects of DDoS preparedness that require improvement. Generally, owing to past conflicts, Israeli financial institutions and government infrastructure have become more resilient and are not as vulnerable to DDoS attacks as they used to be.
At the war's onset, we reached out to our customers, many of whom were already well-prepared due to past conflicts. They have been consistently addressing thousands of DDoS vulnerabilities annually and fortifying their defenses.
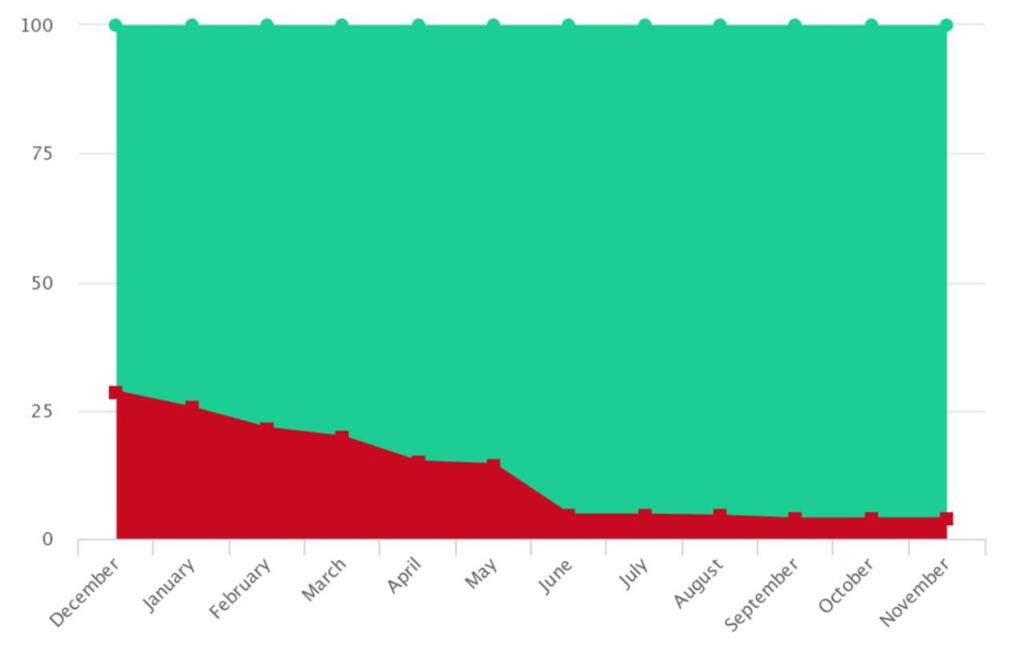
A notable example of an Israeli financial organization's status, similar to others, is illustrated in this graph:
In this example, the green represents fully automated protection, meaning an incoming attack is swiftly repelled. The red represents protection vulnerabilities requiring urgent manual intervention during an attack, with potential for significant damages until the vulnerability is addressed. Initially, the organization had about a 30% vulnerability level (representing over 3200 protection vulnerabilities). Today, it's reduced to less than 3%, signifying that fully automated protection is over 97% effective, a significant increase from the previous 70%.
While a 3% vulnerability might seem substantial and indeed requires improvement, these represent far more complex attacks necessitating sophisticated threat actors. In other words, the threshold for an attack to breach the defenses in the aforementioned example is considerably higher, demanding more intricate planning and execution typically associated with a state possessing advanced cyber capabilities.
Since the conflict began, we've confirmed that some of our organizations were targeted. However, none were impacted by this wave of attacks, despite their persistence, with many lasting hours. Logs show that DDoS defenses automatically engaged, and no emergency manual intervention was needed. There was no disruption to banking, insurance, government or online trading services.
Identifying and continually addressing weaknesses in defenses significantly bolsters protection and is key in preventing damaging DDoS attacks. While nothing is 100% foolproof, the substantial improvement is evident.
Organizations less prepared have a valuable model to follow for the future. Not all have been proactive in preparing for DDoS attacks, leading to disruptions as seen in previous cases. We've observed more significant disruption among these groups, with some publicly disclosing successful DDoS attacks to varying degrees, including:
The Red Alert system experienced several outages. This location-based online system and app alerts Israeli civilians of rocket attacks in their vicinity.
Barzilai Medical Center was offline for 40 minutes, during which no services, patient or doctor information was accessible.
Sheba Medical Center, one of Israel’s largest and most advanced medical facilities, faced a coordinated attack comprising DDoS and intrusion attempts. Consequently, as a precaution, its entire network was disconnected from external access.
The Postal Bank of Israel experienced brief downtime from a DDoS attack, preventing customers from conducting any transactions or activities.
Teva Pharmaceutical Industries' website, along with some of its subsidiaries, was offline for an unspecified period due to DDoS attacks.
“Israel is and will remain a high-value target for malicious threat actors. DDoS attacks can only succeed when vulnerabilities are exploited in the deployed DDoS protection," said Matthew Andriani, CEO of cyber defense firm MazeBolt.
"All Israeli organizations should ensure they are continuously identifying and eliminating such vulnerabilities to prevent having to ever respond to such damage on their online critical services. Providing customers and the public with critical online services, especially in times of crisis, is essential.”
How to protect yourself from DDoS attacks
Think ahead: Adopt a preventative and proactive approach to DDoS cybersecurity.
Multi-layered defenses: Deploy multiple layers of DDoS protection for your organization.
Identify and close weaknesses in defenses: Continuously identify all vulnerabilities in your layers of DDoS protections and close those vulnerabilities to strengthen defenses.
By following the above recommendations, you can prevent damaging attacks and ensure your organization's business continuity remains unaffected during an attack. These guidelines help ensure fully automated DDoS protection is in place and effective when attackers decide to strike.