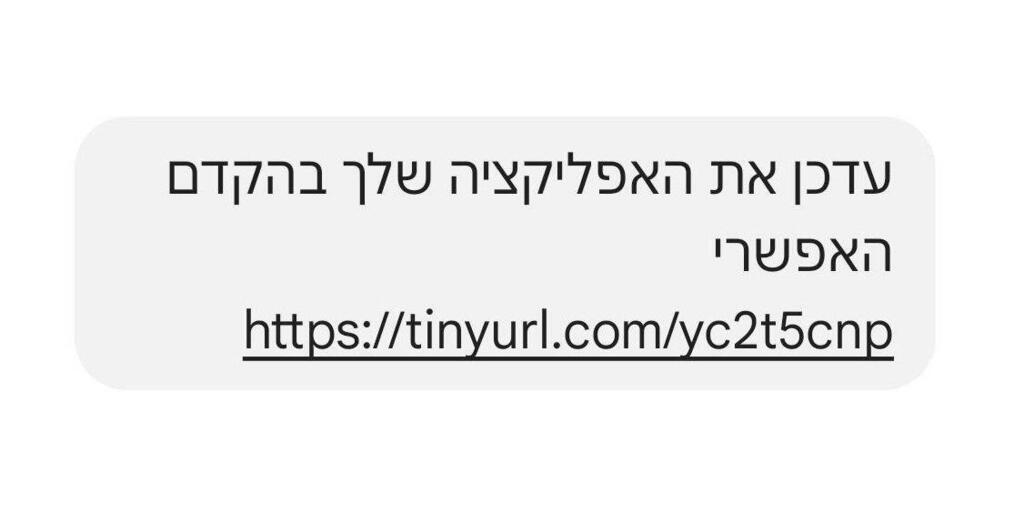
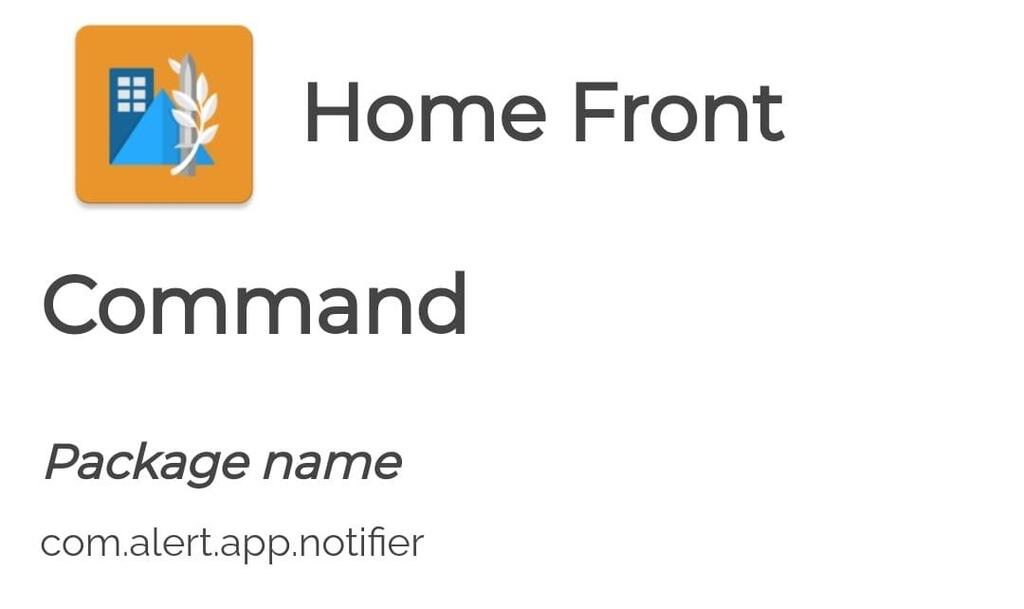
We've got a significant security alert on our hands — a wave of malicious SMS messages, impersonating official bodies like the Home Front Command, hit numerous Israelis on Tuesday night, sparking confusion and concern. The National Cyber Directorate's investigation reveals these messages contain a dangerous link designed to download malware onto victims' devices.
It's suspected that Iranian and pro-Palestinian hacker groups are behind this campaign. They likely exploited a compromised SMS distribution company's infrastructure to send these messages. If you clicked the link but didn't download or install anything, you're probably safe. However, the investigation is ongoing, and more updates may surface.
One of the messages links to the site of the Iranian group Anonymous Sudan, a well-known malicious hacktivist group previously targeting Israel using Russian hacking tools. Recently, two leading members of this group, of Sudanese origin, were arrested at the U.S.'s request in an undisclosed location, facing extradition. But it's unclear if they're the only operators, as suspicions have lingered about hackers possibly acting under Kremlin sponsorship. Identifying hackers definitively is complex, with different groups sometimes using the same names to mislead law enforcement.
The recent campaign included a particularly dangerous message, posing as the Home Front Command. Check Point's analysis shows it's a scam imitating the command's app. "The message urges users to download a new app 'as soon as possible,' masquerading as the Home Front Command app. Our preliminary check confirms it's malicious, downloading directly to smartphones outside official app stores, aimed at compromising the user and their device," the company explained.
Check Point further detailed that "the app can extract account information, read contacts, send SMS messages and alerts, and even operate when the screen is off or in standby mode (via WAKE_LOCK). It can access files on the device (photos, videos, audio) and switch the device to silent mode autonomously, potentially to prevent the user from hearing emergency alerts."
3 View gallery
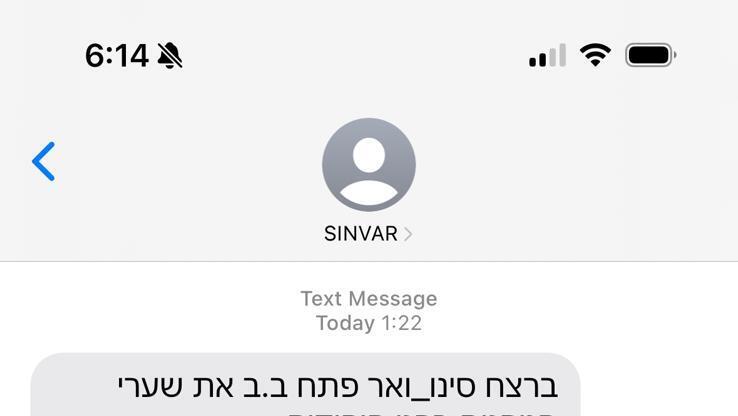

Threatening message under misspelling of killed Hamas leader's name
(Photo: Screenshot)
Another message, sent under the name "sinvar" (a misspelling of Hamas leader Yahya Sinwar's name), threatens revenge, claiming "Sinwar's murder has opened the gates of hell for the Jews," with a link to an Iranian group behind attacks on Israeli governmental and public bodies during the war. Based on past incidents, these messages likely reached a large number of citizens, according to Check Point's assessment.
The Cyber Directorate reported: "We received numerous reports from citizens about SMS messages impersonating the Home Front Command, containing harmful links. Our teams have disabled the link. Our analysis reveals clicking the link led to downloading malware, which could send threatening SMS messages from your number to your contacts."
"If you clicked the link but didn't proceed with installation or grant app permissions, your device is likely unaffected. Generally, only download mobile apps from official app stores. Stay vigilant and report any suspicions to our hotline at 119," the statement advised.
Remember, some malware can infiltrate a phone without file downloads, so always exercise caution. Even if you didn't download anything, closely monitor your device's performance. If it slows down or you encounter issues, consider having it checked by a professional.
Get the Ynetnews app on your smartphone: