Getting your Trinity Audio player ready...
Efforts to find a solution to one of the greatest threats to global cybersecurity — the cracking of encryptions by quantum computers — are making significant progress. The Financial Times reported back in August that the U.S.’s National Institute of Standards and Technology (NIST) is set to introduce three algorithms designed to create encryption that could withstand the power of a quantum computer, thereby protecting strategic assets and preventing their collapse.
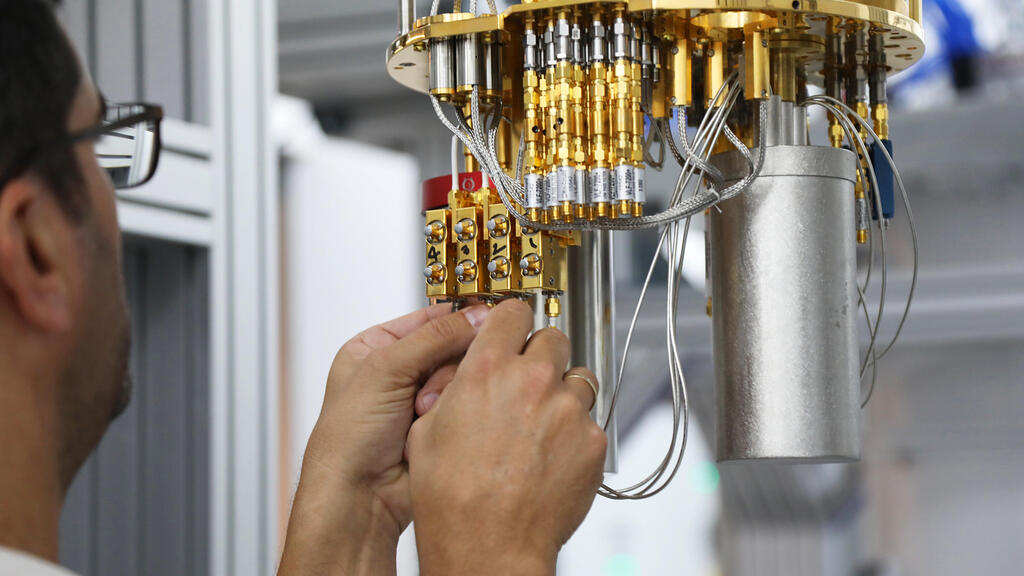
Quantum computers possess extremely powerful computational power. Unlike traditional computers, where each bit can be either 0 or 1, in quantum computers, each qubit (Qbit) is in a "superposition," meaning it can be 0, 1, or any number of states in between, vastly enhancing its computational capabilities.
This ability led Google, as early as 2019, to declare "quantum supremacy" when its experimental quantum computer completed a calculation in 200 seconds that would take the most powerful current computer 10,000 years.
Although quantum computers are still in development, their potential is rapidly growing. They’re expected to hit the market within a few years and there is a concern that, alongside their enormous benefits to humanity, they could also pose a significant risk by being able to crack any existing encryption, including that of global banking systems and national security agencies. The day this becomes possible is referred to as Q-Day.
In preparation for Q-Day, NIST has led an effort to develop a technology known as post-quantum cryptography. The idea is straightforward: since quantum computers don’t exist yet, we need to develop an encryption algorithm that runs on a conventional computer but is still resistant to a quantum computer's capabilities.
The world's most common encryption algorithm, RSA, was developed by Israeli Prof. Adi Shamir and his two American colleagues. It’s currently used to protect all digital information worldwide — from emails and WhatsApp messages to intelligence data and battle plans. Cracking RSA encryption with a regular computer could take decades. A quantum computer could do it in seconds.
Apple to use algorithm to protect users
NIST issued a call for research groups worldwide to present alternatives to RSA, algorithms that would be quantum resistant. Many proposals were submitted from across the globe, but most were ultimately broken when other researchers demonstrated a quantum algorithm that could crack them.
Three algorithms that appear particularly resilient have reached the final stage. Once officially approved, all U.S. government agencies will be required to implement them and private sector companies are expected to follow suit. Apple was quick to announce in February that iMessage data would be protected by post-quantum encryption.
Experts explain the urgency due to the concern of a "collect now, decrypt later" strategy: criminal organizations or intelligence agencies could obtain encrypted files today and decrypt them once quantum technology matures. This is why many companies are seeking to encrypt their data with quantum-resistant encryption even though quantum computers don't yet exist.
Nir Minerbi, CEO of the quantum software company Classiq Technologies, said, "NIST and other organizations have been working on this issue for several years. The challenge is to develop protocols that we believe are resistant to quantum computing and the next step is to implement them across modern computing systems. This is a multi-year effort costing hundreds of billions."
Will the presented algorithms be resistant to quantum decryption?
"The short answer is 'no.' To elaborate, some Chinese researchers published an incredibly complex quantum algorithm that suggested a way to crack NIST's algorithm using a quantum computer.
“For two weeks, the entire quantum computing community felt that the last hope against quantum computing was snuffed, but then it was discovered there was a mistake in the Chinese algorithm. This demonstrates how fragile this matter is—it could turn out that the algorithm is crackable at any moment."
The only way to fully counter a quantum computer might be with another quantum computer. This involves a technology known as "quantum encryption." The theoretical concept, known as Quantum Key Distribution (QKD), uses quantum entanglement, where a mysterious connection is formed between subatomic particles even if they’re far apart.
In other words, this means that with such encryption any unauthorized attempt to access the data can be immediately detected.
Dr. Tal David, co-founder of the quantum computing company Quantum Art, explained that post-quantum algorithms are advancing alongside the development of quantum encryption systems like QKD.
"These technologies complement each other. If you're a government entity that wants to protect highly sensitive information you need to protect yourself today because malicious entities will gather the information now and decrypt it when they can. In such a case, you'll probably want to equip yourself with both post-quantum algorithms and QKD."
So, are post-quantum algorithms weaker than QKD?
"Currently, no quantum algorithm is known that can deal with post-quantum methods. But that doesn't mean there won't be one. On the other hand, QKD systems are protected at the physical level and therefore can’t be hacked."
Shlomi Cohen, a consultant in cybersecurity and quantum fields and former CEO of the Israeli quantum encryption company HEQA (formerly QuantLR), noted that current encryption capabilities have lost their strength.
"If you look into penetrations into financial institutions, banks are breached frequently, although most breaches aren’t publicized. However, there are financial institutions, especially in New York, that encrypt the data transmitted between the main branch and the backup site in New Jersey using quantum encryption at a level that can’t be penetrated."
Does post-quantum encryption make quantum encryption unnecessary?
"The transition from mathematical to quantum encryption will take a long time, which is why some say post-quantum encryption would be used during the transition period. My estimation is that the post-quantum period will be shorter than expected and it’s not advisable to rely on post-quantum encryption. When you look at what companies like Amazon, Nvidia, Boeing and Grumman are seeking you can see that most are skipping the post-quantum stage."
Yotam Ashkenazi, Accenture Security Israel’s innovation director, added, "The path to implementing the algorithms selected by NIST is far from simple. The transition process isn’t just about integrating new technology; it involves a fundamental overhaul of existing systems, updating and rewriting code across a wide range of applications and upgrading infrastructure to fit the new cryptographic algorithms.”
“The transition requires a significant investment of time, resources and skilled manpower. The process isn’t only a technological challenge but also a complex strategic project for the industry, requiring long-term planning and extensive collaboration between companies, regulators and experts in the field,” he explained.