Getting your Trinity Audio player ready...
Last month’s exposure of Elimelech Stern’s activities as an Iranian agent got everyone’s imagination going. The 21-year-old from Beit Shemesh was recruited by Iranian intelligence via a seductive Telegram profile using the name Anna Elena. He was assigned shocking missions such as setting a forest fire, vandalizing property, sending people threats, and more.
The police and Shin Bet issued an unusual statement detailing the capture of Stern and two of his collaborators. The Shin Bet referred to nothing short of an "Iranian intelligence infrastructure."
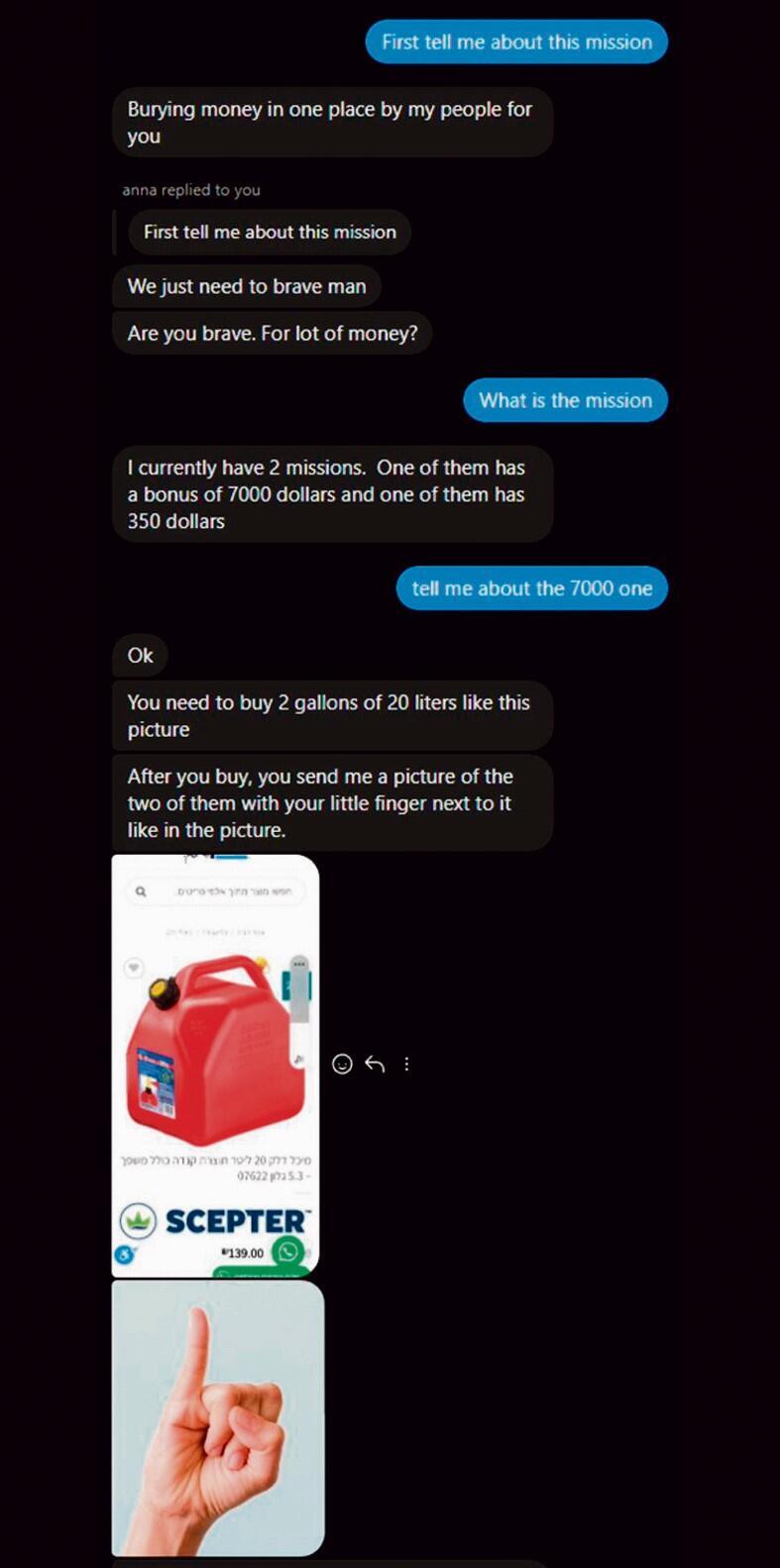
According to the indictment filed against him, Stern operated as a go-between recruiting two further agents and paying them for hanging up posters (and not the good kind) in Tel Aviv, and receiving payment from his handlers in Bitcoin. The most disturbing mission he was assigned was sending a sheep’s head to the home of Israel’s ambassador to the UN’s IAEA (International Atomic Energy Agency) which oversees Iran’s nuclear capabilities.
This story has all the hallmarks of a good spy story, but has it all been blown out of proportion? Stern is a Vishnitz Hasid with an interest in cryptocurrency, not a Fauda type. His main sin, God help us, was having a non-kosher phone (smartphone) on which the Iranians contacted him, and displaying Bitcoin proficiency that’s not on the Vishnitz curriculum.
That being said, he couldn’t find a sheep’s head in any shop, so he was instead instructed to place a sheep doll and a knife at the designated location. It looked more like a bag grandma had left behind than a threat to the IAEA. He was also asked to smash a car window at a protest, set fire to a forest, and murder an Israeli, but opted out of that one. Stern said that he just wanted to learn more about Bitcoin. “I didn’t think I was dealing with a hostile or dangerous element.”
It's doubtful that this operation will appear in Iranian intelligence’s hall of fame. On the Israeli side, however, these incidents raised enough concern for the Shin Bet to issue a warning to the public asking everyone, especially yeshiva students and the wider Haredi community, to remain vigilant. the Ultra-Orthodox community has become a target for the Iranians due to their lack of familiarity with the dangers of the Internet and their opposition to the IDF draft and the army in general.
We spoke about the incident with Lior Ben Gigi, head of the cyber security division at an Israeli hi-tech company. The company deals with software for large organizations, including cyber security. Ben Gigi tells us that this incident first came to light when an IDF soldier targeted by the Iranians contacted Neria Levi, a consultant at the company, describing a "relationship that had developed between him and a user named Anna Elena."
"He said he suspected there was something criminal about it," said Ben Gigi. "Neria said that the nature of the communication seemed less criminal, and continued the exchange to see where it was going. Where it went left no room for doubt. Initially, there were efforts to determine his political orientation, and then came monetary offers in exchange for missions such as setting fire to forests, vandalizing cars, and creating provocations at demonstrations. At this stage, we decided to contact the security authorities and from there, it was a short leap to finding the next victim – Stern, the yeshiva student.”
"It has soared by thousands of percent since the war. These numbers are unprecedented. We’re working around the clock hopping from one incident to the next. It generally doesn’t get as far as recruiting agents. Most of these cases, unfortunately, are not cleared by the censor for publication," added Ben Gigi.
Could there be Israelis among us operating for the Iranians and we don’t know?
"My conservative estimate is that thousands, if not tens of thousands, of Israelis have received messages - whether or not they were aware of it. The thing is that they sometimes carry out missions without knowing they’ve been recruited by the Iranians. In most cases, recruiters don’t identify themselves as Iranian, but rather misinform Israelis into thinking they’re doing it for reasons other than operating against Israel. And there are lots of these cases. You’d be surprised quite how prevalent it is.“
Until a decade ago, Iranian espionage efforts to recruit agents in Israel didn’t work so well. Security authorities arrested a series of Iranian spies engaged in espionage against Israel including a Belgian citizen of Iranian descent; Israeli citizens (Gonen Segev being the most infamous); Israelis from Iran; extremist Haredim; and Palestinians both from Israel and the West Bank.
Iranian intelligence seems to be concentrating on recruiting agents over social media. In 2022, we learned that four Israeli women of Iranian descent along with one of their husbands had been recruited via Facebook.
Their handler, posing as a Jew in Tehran, paid them thousands of dollars for photographs of the U.S. embassy and security guards at a mall in Holon, collating details of Jews of Iranian descent in Israel, and even efforts to contact Likud MK Keti Shitrit.
The handler also asked the women to convince their sons to enlist in IDF intelligence units, to get more information out of them in the future. Indictments were filed against the five, the court acquitting four of them ruling they had been innocent victims.
A further incident emerged the same year when the Iranians made efforts to cajole Israeli officials: academics, businesspeople, journalists, and members of the defense establishment to leave for Europe to kidnap them there. The Shin Bet cautioned that Iranian intelligence had made numerous attempts to recruit Israelis over the internet. The Elimelech Stern case has received far less attention, Prime Minister Benjamin Netanyahu is not addressing the matter.
How many similar incidents since 2022 have gone undetected? Perhaps some were detected and not publicized. We contacted The National Cyber Security Authority (NCSA) and the Shin Bet who both declined to comment. Ben Gigi explains the modus operandi: "They know how to target people. They don’t contact people arbitrarily, but rather specifically seek out soldiers who have been in Gaza and members of the Haredi community who are less exposed to the media. They transfer payments via Bitcoin and there’s no way of tracking it."
The use of cryptocurrency for transferring money to fund terrorism is one of the greatest challenges law enforcement authorities face across the globe. Iranian intelligence makes sophisticated use of Bitcoin, making it very hard to detect the source of the money. Ido Ben Natan, CEO of Blockaid, a company specializing in cyber protection of crypto payments, said that the company has detected numerous incidents of transfer of payments to fund terrorism by Bitcoin and other cryptocurrencies.
"We’re looking at an increase in the use of cryptocurrency for terrorism. What we see here is one of many cases of paying people for activities. This time it was ‘successful’ and the money went through. Iran and other countries are constantly operating against us, trying to attack us in a thousand and one different ways. This was one of many," he said.
Blockaid has developed technology to protect crypto companies and their users from hacking and fraud. The company recently identified a website claiming to be collecting donations to support Israel, but that was used to hack into unsuspecting users’ crypto wallets.
Can transferring money by crypto be stopped by, let’s say, going into virtual wallets?
"In this case, they contacted an individual curious about crypto because he knew how to use the crypto technology. Although it’s improving, this technology isn’t simple enough for the ordinary person to use. Think of crypto like transferring cash. You can’t stop a cash transfer after it’s occurred. This is how crypto works. A solution such as ours can detect threats and efforts to transfer money that shouldn’t be transferred. We also monitor the course the money takes across the world, follow the wallets and if the money sits in an exchange we work with, we can stop it from being converted from Bitcoin into shekels or dollars."
Are the security authorities successful in averting the flow of crypto money into Israel?
"The Israeli security authorities are trying to understand how to address it. There are things they can do, but there are obviously things that are new and outside of their understanding. They do what they can with the tools they have and are constantly improving. But attacking is much easier than defending.”
Iranian activity on social media seems to have intensified considerably since October 7. Experts in the fields said the Iranians are trying to influence people as a wide-scale effort to divide and create discord, evoke provocations, increasing the divide between Israelis. And this is happening right now over social media.
Iranian handlers are good at identifying fracture points in Israeli society and stirring up hatred using topics connected to the hostages, the protests, and incitement against the Brothers in Arms protest faction. They target their messages personally at users who frequently echo them, increasing their social media exposure and sowing confusion. This may lead certain people to commit irrational acts, like collaborating with Iranian agents.
One Israeli organization keeping tabs on events is FakeReporter, which exposed Iranian efforts to influence people via social media as early as 2021. FakeReporter CEO Achiya Schatz said that this has very much increased since October. The main problem is that it’s difficult to identify fake profiles. Once, fake profiles had no friends, no content, and no pictures. Another giveaway was botched Hebrew. But all this seems to have changed now. Their language has improved remarkably by using AI tools, and they create much more content using better language” said Schatz.
Ben Gigi said, "They hack into users’ accounts and activate them. They have friends and postings and it's very hard to detect. It could be a profile of someone still posting and they’ll have no idea that their identity is being used by someone else. We’re talking about capabilities at state, not criminal organization, level.”
What can be done to address the danger?
"You have to be mindful of the nature of the communication, not just whether the guy has friends and a picture. If the text looks strange and if the things they’re suggesting seem off. We’re taking steps to increase customer awareness, and I keep being contacted by people receiving problematic messages. The Iranians have a decent cyber system and they’re working very hard to bring us down to undermine the regime from within."
"They blossom when we wither. When we have division, polarization, and hatred, they get in there and try to further polarize and radicalize. We’ve been seeing this since the war began. It’s a very smart move: Undetected and unexposed, they sow fear and anxiety in the general public and make people think they’re everywhere and that anyone might be an Iranian bot," Schatz said.